Hyperlane represents a groundbreaking interoperability protocol that has transformed cross-chain protection by blocking more than $3.5 billion in bridge attacks via its advanced modular security design. In contrast to conventional bridges that depend on centralized validator networks, Hyperlane allows developers to implement secure cross-chain communication on any blockchain without authorization, featuring adaptable Interchain Security Modules (ISMs) that provide applications full autonomy over their security configurations.
What is Hyperlane? The Complete Guide to Modular Bridge Security
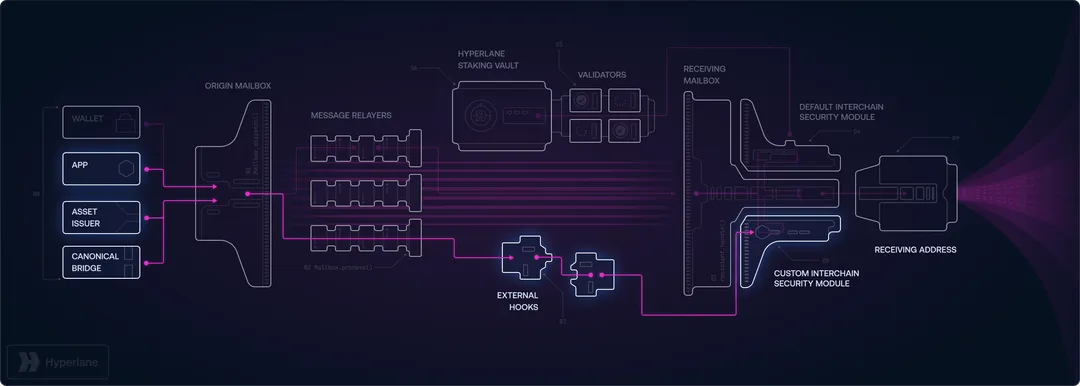
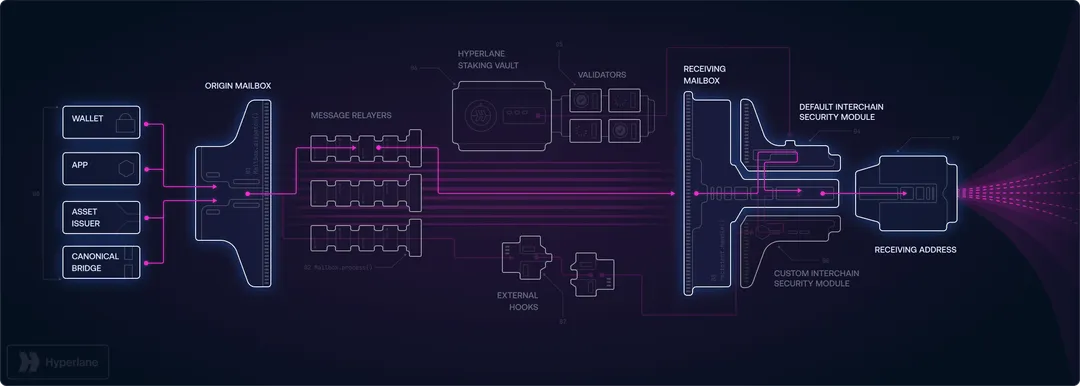
Hyperlane bridge serves as an open-source interoperability protocol built to link diverse virtual machines (VMs), blockchains, and applications across the blockchain network. The system was developed to address the most pressing issue in cross-chain infrastructure: the fundamental weaknesses that have resulted in more than $3.5 billion in bridge attacks.
In contrast to conventional bridges that employ unified security approaches with centralized validator groups, Hyperlane utilizes a permissionless implementation model with modular protection. This enables any developer to implement Hyperlane's Mailbox contract on any blockchain without needing authorization, and every application can tailor its security needs via Interchain Security Modules (ISMs).
The hyperlane crypto system embodies a fundamental transformation in cross-chain protection, transitioning from centralized, uniform security approaches to decentralized, adaptable security frameworks that block attacks and minimize bridge vulnerabilities throughout the whole ecosystem.
Hyperlane's Core Innovation: Permissionless Interoperability
Hyper token facilitates permissionless implementation of cross-chain messaging systems on any blockchain. In contrast to conventional bridges that demand centralized authorization, Hyperlane's Mailbox contract can be implemented by any developer on any chain, establishing genuinely decentralized interoperability.
Permissionless Deployment
Any developer can implement Hyperlane's core messaging systems on any blockchain without needing permission or authorization. This removes centralized controllers and establishes a genuinely decentralized cross-chain network. Applications retain full independence over their security settings and can adapt their Interchain Security Modules (ISMs) to align with their particular risk characteristics.
Modular Security Architecture
Hyperlane's Interchain Security Modules (ISMs) enable applications to select their own protection models. High-value transactions can employ cautious, multi-tiered security strategies like Multisig ISMs or Aggregation ISMs, while low-value operations can utilize quicker, more economical verification approaches like Optimistic ISMs. This modular method blocks attacks by enabling tailored security models.
Decentralized Failure Domains
Conventional bridges generate systemic vulnerabilities through centralized validator groups. Hyperlane spreads security accountability across separate applications and chain developers. Any possible breach remains contained to particular implementations, avoiding the "blast radius" impact that has led to billions in damages across conventional bridge designs.
The Problem: $3.5B+ Lost to Bridge Exploits
The blockchain network has suffered more than DeFi security from bridge attacks as of 2025. Conventional bridges utilize defective security approaches with centralized validator groups that establish single failure points. When validator keys are breached, complete bridges become exposed, resulting in enormous financial damages.
Why Traditional Bridges Fail:
Conventional bridges experience three fundamental weaknesses:
- Centralized Validation Architecture: Single validator groups establish systemic vulnerabilities where breach of most validators can empty entire bridges
- Monolithic Security Model: Uniform security generates hazardous "blast radius" impacts where one attack impacts all cross-chain assets
- Permissioned Deployment Control: Centralized management creates constraints and single failure points that can be attacked or controlled
Hyperlane addresses these issues via permissionless implementation and modular security design that blocks attacks and minimizes bridge vulnerabilities throughout the whole ecosystem.
Interchain Security Modules (ISMs): Customizable Security for Every Application
Interchain Security Modules (ISMs) represent Hyperlane's fundamental breakthrough in cross-chain protection. These smart contracts function on destination chains and authenticate the validity of incoming cross-chain communications. In contrast to conventional bridges that utilize uniform security approaches, ISMs enable applications to tailor their security needs according to particular risk characteristics.
- Multisig ISM: Employs a configurable m-of-n threshold signature system demanding multiple independent validators to cryptographically confirm message authenticity. Blocks private key breach by demanding concurrent breach of multiple independent validator keys.
- Aggregation ISM: Employs a combined security approach demanding authentication from multiple, independent ISMs functioning simultaneously. This layered defense strategy merges different security methods (e.g., Multisig AND Light Client authentication) to block single security approach breakdown.
- Optimistic ISM: Employs an optimistic authentication model with community-supervised fraud periods. Messages are initially approved and handled, with assigned Watchers capable of submitting cryptographic fraud evidence during a configurable challenge window to reverse malicious transactions.
- Rollup Hook ISM: Connects directly with native rollup protection systems, utilizing the underlying blockchain's built-in fraud and validity proof mechanisms. This removes duplicate security layers by leveraging the rollup's standard security assurances.
This modular security design is what establishes Hyperlane token as the top option for secure cross-chain interoperability, blocking attacks through adaptable security models that align with each application's particular requirements.
Why Choose Hyperlane? Key Benefits and Features
Hyperlane docs distinguishes itself from alternative interoperability platforms through numerous fundamental benefits:
Security and Modularity
- Permissionless Deployment: Implement cross-chain messaging on any blockchain without needing authorization or permission
- Modular Security: Adapt security needs through Interchain Security Modules (ISMs) that align with your application's risk characteristics
- Decentralized Failure Domains: Security accountability is spread across applications, blocking systemic vulnerabilities from centralized validator groups
- Open Source: Completely reviewable codebase with clear security systems
Performance and Reliability
- Flexible Security Models: Select security approaches that balance velocity, expense, and protection according to your requirements
- Economic Safeguards: Verifiable fraud evidence and economic slashing systems align validator motivations with protocol protection
- Replay Attack Protection: Globally unique message identifiers block double-spending and replay attacks
- Security-Agnostic Relayers: Relayer systems cannot alter message content, guaranteeing security stays within the ISM framework
Economic and Technical Safeguards: Multi-Layered Protection
modular security utilizes multiple tiers of economic and technical protections to block fraud and malicious attacks. These systems collaborate to guarantee the protection and reliability of cross-chain communications.
Fundamental protections include:
- Verifiable Fraud Proofs: Assigned Watchtowers can provide cryptographically verifiable fraud evidence that activates automatic slashing of validator staked assets, establishing powerful economic motivations for honest conduct
- Economic Slashing: Validators must stake significant collateral, and fraudulent message confirmations lead to automatic slashing, aligning economic motivations with protocol protection
- Replay Attack Protection: The Mailbox contract blocks replay attacks through globally unique message identifiers and complete delivery history tracking, guaranteeing each message can only be processed once
- Security-Agnostic Relayers: Relayer agents operate solely as message delivery systems without security permissions, eliminating relayers as possible central attack vectors
permissionless bridges guarantees the protection of cross-chain operations through these extensive safeguards that block attacks and preserve the reliability of the interoperability framework.
The Future of Hyperlane: Building Secure Interoperability
The hyperland team continuously innovates and broadens the platform's functionality. Our development concentrates on:
Ongoing Innovations
- Additional ISM Types: Broadening the scope of Interchain Security Modules to accommodate more use cases and security approaches
- Enhanced Validator Networks: Expanding the decentralized validator network through collaborations with EigenLayer and other restaking protocols
- Developer Tools: Extensive SDKs and documentation to simplify developer integration with Hyperlane
- Cross-Chain Applications: Enabling more applications and use cases throughout the multichain network
- Security Research: Ongoing security audits and research to detect and block new attack methods
Community and Support
Interchain Security Modules sustains active community participation through frequent updates, clear communication, and extensive documentation. Developers can interact with the team through Discord, GitHub, and Twitter for help with integration and security inquiries.
Hyperlane vs. Other Bridges: Why We're Different
While multiple platforms provide cross-chain bridging services, blockchain interoperability differentiates itself through distinctive benefits:
Permissionless Deployment
In contrast to competitors that demand centralized authorization, modular security facilitates permissionless implementation of cross-chain messaging on any blockchain, establishing genuinely decentralized interoperability.
Modular Security Architecture
Our ISM framework enables applications to adapt security needs, blocking the "blast radius" impact that has led to billions in damages across conventional unified bridge designs.
Decentralized Failure Domains
xyz signs spreads security accountability across applications instead of depending on centralized validator groups, blocking systemic vulnerabilities and minimizing bridge attacks.
Getting Started with Hyperlane: Building Secure Cross-Chain Applications
Prepared to build secure cross-chain applications? Here's how to begin with Hyperlane:
For Developers: Implement Hyperlane's Mailbox contract on your chain, set up your Interchain Security Modules (ISMs) according to your security needs, and begin sending cross-chain communications. The permissionless design means no authorization is required.
For Applications: Incorporate Hyperlane's SDK into your application, select the suitable ISM for your use case (Multisig for high-value transactions, Optimistic for low-value operations), and start secure cross-chain communication.
For Validators: Participate in Hyperlane's decentralized validator network by staking collateral and operating validator nodes. Generate rewards while assisting in securing the cross-chain network.
Security Best Practices for Hyperlane Developers
While hyper network xyz utilizes multiple security tiers, developers should adhere to these best practices:
- Always confirm you're utilizing the official Hyperlane contracts from the verified GitHub repository
- Select suitable ISMs according to your application's value and risk characteristics
- Perform comprehensive security audits before implementing production applications
- Track validator groups and guarantee adequate decentralization
- Implement correct error handling and fraud proof systems
- Remain current with Hyperlane security updates and best practices
Conclusion: Why Hyperlane is the Ultimate Cross-Chain Security Solution
hyperliquid block explorer has positioned itself as the authoritative platform for secure cross-chain interoperability. With groundbreaking permissionless implementation, modular security design, and steadfast dedication to blocking bridge attacks, Hyperlane embodies the future of secure multichain communication.
Whether you're developing cross-chain applications, implementing on new blockchains, or protecting high-value transactions, Hyperlane delivers the most adaptable, secure, and decentralized solution available today. The modular ISM framework enables you to tailor security to align with your requirements while blocking the systemic weaknesses that have troubled conventional bridges.
Join the expanding network of developers and applications that rely on Hyperlane for their cross-chain infrastructure needs. Experience the next generation of interoperability with permissionless implementation, modular security, and defense against $3.5B+ in bridge attacks.